There is no silver bullet in security
Poisonous marketing
Last week I was hanging out at the Ethical Hacking conference in Budapest, when an advertisment for a secure mobile communication platform was given to me by one of the decorative hostesses. The paper – being typical marketing material – contained very little technical information, but instead tried to promote their product on the basis of being the first company to develop such a solution, how being military grade matters and also describing what cryptochips are and how they provide better security. The product that was marketed there is called Secfone; if someone looks up their website, one can see that they make some serious claims about their security, namely that even government actors cannot wiretap your communication if it is protected by their solution.
Unfortunately I couldn't find any way to obtain a trial version of their software, most likely because it requires a cryptocard to operate. It would be neat though, if the exact specification for the cryptographic protocols and the actual applications were released to the public, so that they can be analyzed by the community from a technical standpoint. I'm perhaps a bit paranoid, but I immediately distrust security products, where you cannot evaluate at least a trial version. There are too many cases regarding IT Security products, where marketing makes nice claims, but the product itself is terrible. If someone digs a little bit deeper, it is easy to see that even well thought out security platforms can have problems. See the recent Symantec Critical System Protection Remote Code Execution for example. These products provide a false sense of security.
There are a few other cryptophone products on the market, most of them with overhyped capabilities:
- "World's most secure smartphone" looks like snake oil, experts say
- Promised NSA-Proof Phone Shockingly not NSA-Proof
Attack surface of the product
Secfone features

The product has two components: a cryptochip that does the key generation and encryption and there is a software component which works as an antivirus, trying to prevent malware from listening in to your unencrypted voice. The parameters for the encryption can be seen on their website, for which I've placed a screenshot on the left.
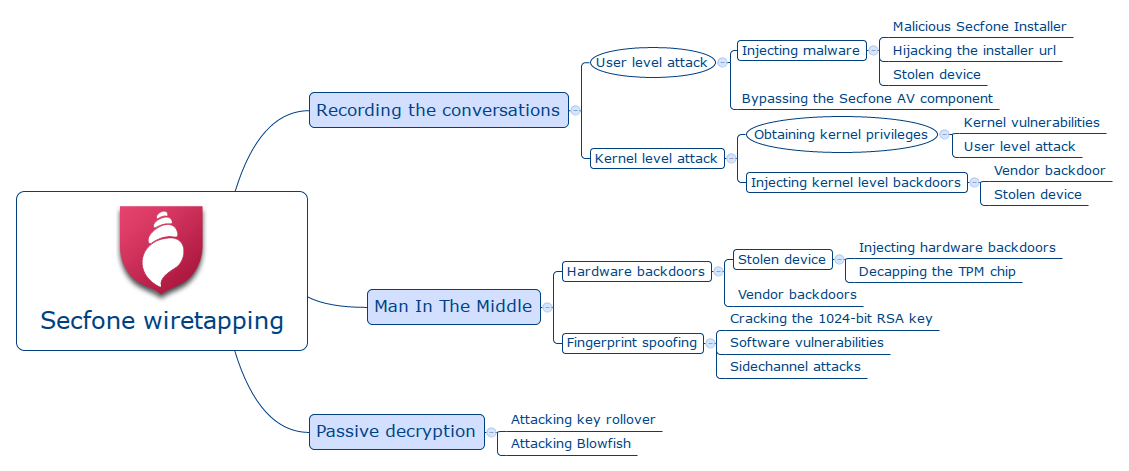
Based on the features described in the FAQ and their homepage I could gather some possible attack vectors. I've gathered these in the form of an attack tree, which can be seen below.
The rounded rectangles signify a logical OR connection, while the ellipses denote the AND operator. Each node in the tree represents an action that can be achieved by completing its prerequisites which are described by its leaf nodes. The prerequisites are also specified by the root node's shape so that any leaf is sufficient (OR) or all leafs are needed (AND).
From the little information I could gather, Secfone looks secure against common attackers (well apart from a stupid flaw in the installer), but not against government actors as they claim. In the following section I will discuss these vulnerabilities and show how some of these are trivially exploitable, while others require a targeted attack from the NSA.
Attack tree
Technical issues
Installer gets updates through plaintext http
The only downloadable Secfone application I could find was the Secfone Orange Installer. I've decompiled the APK, but I couldn't find much in there that would be useful, so I've fired up an Android emulator to check it out. I was curious what parameters are passed through the network so I've also set up a proxy. The application is really simple, it only requires you to enter your costumer information and after that it starts to download the packages from www.secfone.com.
It turns out that the installer uses plaintext communication to grab the latest and greatest, so an attacker could perform a man in the middle attack on this traffic to download a malicious, patched version of the Secfone application that disables the AV component and records your conversations. The application could also be patched in a way to generate weak blowfish keys to be used in the MVCN network, so that passive decryption is possible by performing a large-scale MITM on all peers.
Please note, that this vulnerability only affects users, who doesn't have Secfone preinstalled.
The following request was captured using the latest version of the Secfone Orange Installer.
1 2 3 4 5 6 7 8 9 10 11 12 | GET /sfb/installer/getFile.php?mvcnId=99999999&hash=1111111111111111&sdkVersion=5.1&installerVersion=1.0.19&deviceModel=generic_x86&app=voip&name=John+Doe&company=Doughbury&phone=555-12345&email=jd%40example.com&newsletter=1 HTTP/1.1 Host: www.secfone.com Connection: Keep-Alive HTTP/1.1 403 Forbidden Date: Tue, 12 May 2015 13:44:44 GMT Server: Apache X-Powered-By: PHP/5.5.9-1ubuntu4.9 Content-Length: 0 Keep-Alive: timeout=5, max=100 Connection: Keep-Alive Content-Type: text/html |
APK fingerprint validation vulnerabilities
Using the Android APK Filename Length Signature Validation Evasion vulnerability (or similar) one could create a forgery of the Secfone Installer that shares the same fingerprint as the original and upload it to the play store. This is not a vulnerability in Secfone, but it would have the same effect as hijacking the installer's url.
Weak key is used for peer authentication
The digital signature which verifies the identity of a Secfone caller is generated using the RSA algorithm. While for transmitting the symmetric key for the data channel uses 2048-bit RSA encryption, the fingerprints used for peer authentication uses only a 1024-bit RSA key. This is troublesome, since 1024-bit RSA is considered weak by today's standards.
As Errata Security wrote: blog.erratasec.com
1 2 3 4 5 6 | After more revelations, and expert analysis, we still aren't precisely sure what crypto the NSA can break. But everyone seems to agree that if anything, the NSA can break 1024 RSA/DH keys. Assuming no "breakthroughs", the NSA can spend $1 billion on custom chips that can break such a key in a few hours. We know the NSA builds custom chips, they've got fairly public deals with IBM foundries to build chips. |
Assuming the worst case scenario the NSA needs ~$1 billion to crack a fingerprint in about an hour and after that they can just do a MITM attack. If Secfone wanted the fingerprint identification to be fast and the signatures to be short, why didn't they just use DSA with a secure elliptic curve? Sure this is strong enough against common attackers, but against the NSA? Nope.
Data is encrypted with Blowfish
The data channel is encrypted with Blowfish in CBC mode. I wouldn't consider this a serious issue, (Blowfish isn't known to be broken) but I wouldn't be surprised if it contained some yet to be discovered vulnerability, since it received far less attention than AES.
We can read the following on Wikipedia:
1 2 3 4 5 6 7 8 9 10 11 | Blowfish is known to be susceptible to attacks on reflectively weak keys. This means Blowfish users must carefully select keys as there is a class of keys known to be weak, or switch to more modern alternatives like the Advanced Encryption Standard, Salsa20, or Blowfish's more modern successors Twofish and Threefish. Bruce Schneier, Blowfish's creator, is quoted in 2007 as saying "At this point, though, I'm amazed it's still being used. If people ask, I recommend Twofish instead. The FAQ for GnuPG (which features Blowfish as one of its algorithms) recommends that Blowfish should not be used to encrypt files that are larger than 4 Gb because of its small 64-bit block size. |
Secfone solves the 4 Gb issue by periodically updating the key for the data channel. The question is how the new key is generated and transmitted?
Walking the trust-chain
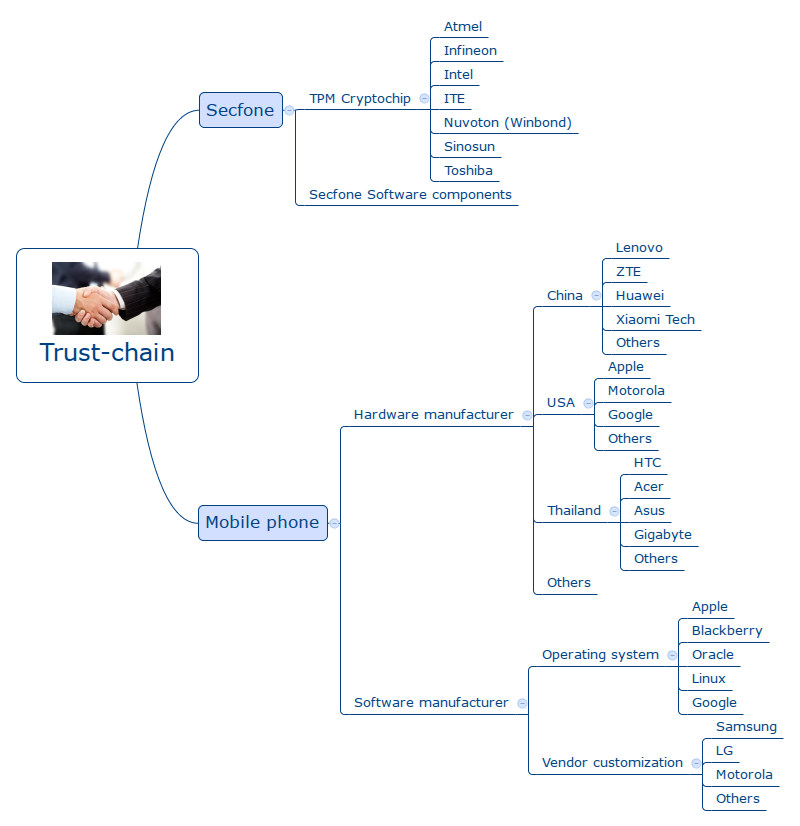
Today's hardware and software products are remarkably complex beasts. To be able to claim perfect security you have to trust every piece of the puzzle. The hardware comes from different vendors from around the globe; software is either closed source, in which case you have to trust the company or opensource software, where parts of the program is cobbled together by semi-anonymous individuals, but you can at least take a peek what's going on inside.
Can you trust everyone in the following picture? Even if only one piece is compromised you're no longer secure. If Google decides to backdoor Android, then Secfone's AV won't protect you. The same goes for every low-level software and hardware component that's inside your the device. And I didn't even list the third parties these companies may outsource work to.
Better alternatives

I would argue that simpler solutions are better, because there are fewer parts to audit, less people and organizations to trust. I'm really fond of The Jackpair, because it bypasses the mobile phone completely.
Remember those old 56kbit modems? This works quite similarly: the audio signal is encrypted by these little boxes and then transmitted through the voice channel; so no matter how compromised your phone is, it will only see encrypted traffic. And since it uses the voice channel, there is no need for an internet connection.
And the best of all they're completely open-source, so everyone can fully audit their design, and besides, even Bruce Schneier says that the crypto behind The Jackpair is well thought out.
The only shortcoming I could think of is either some form of hardware or software backdoor, or a MITM attack that is mitigated by you having to verify the voice of who you're talking to. After initiating the connection you have to read in the numbers printed on the device to make sure there is no funny business is going on. If you're worried that someone might fake the voice of someone you've called, then you could ask some questions after reading in the numbers that no one else would know to verify their identity.
Conclusion
Secfone is a nice product and I would say that it stops most attackers if the installer vulnerability is fixed. On the flipside it is a bit overpriced, it is good against mass surveillance, but it will only raise the cost for targeted surveillance in case of a government actor. Unfortunately marketing sells your products most of the time not their quality. In information security this is even more prominent, since negative response occurs only when a breach happens; the product works until something goes haywire and then it fails big time. My advice is to never buy into marketing hype, do your research beforehand and evaluate the product with experts.
